Encrypted GPS M-Code: It’s Here, and It’s Critical
MULTI-TASKING? LISTEN TO THIS ARTICLE INSTEAD
Global Navigation Satellite Systems (GNSSGlobal navigation satellite system (GNSS): A general term describing any satellite constellation that provides positioning, navigation, and timing (PNT) services on a global or regional basis. See also), particularly the US Global Positioning System (GPSGlobal Positioning System is a navigation satellite system. See also), are an ever-present feature of modern life. However, they provide much more than simply the positional information that most people associate them with, and which anyone with a GPS-enabled smartphone is aware of.GNSS are currently the principal source not only of locational data, but also highly accurate timing, providing what is known as PNTPosition, Navigation, and Timing: PNT and map data combine to create the GPS service. –Positioning, Navigation, and Timing. It is unlikely that any modern military mission could be successfully executed without accurate PNT.There are four major GNSS: GPS, the US system; the 24-satellite Russian GLONASS, which was refurbished in 2012; the 24-satellite European Union Galileo system; and the 35-satellite Chinese Beidou system. To these can be added the Japanese (QZSSQZSS is a regional satellite system in the Asia/Pacific Region. Developed and maintained by the Japanese government, this satellite constellation provides similar services as GPS: location, navigation and timing.) and Indian (NAVIC) regional systems.GNSS rely on small receivers detecting transmissions from satellite constellations, which, through triangulation of a number of these signals, allow the very accurate calculation of the location of the receiver. The GPS constellation, for example, enables a user to view at least four satellites. Additionally, time signals are transmitted from the satellites, which enables the receiver to calculate local time precisely.
GNSS, particularly GPS, is the most important source of PNT for military users. It provides supremely accurate position and timing, with the latter linked to atomic clocks monitored by the GPS ground control segment and traceable to Universal Coordinated Time (UTC) at the US Naval Observatory. PNT provided by GPS is fundamental to precision-guided weapons, the provision of synchronized situational awareness, the control and navigation of unmanned platforms, and almost every area of military activity.
The significance of accurate and common location and navigation data is obvious, but the importance of accurate and common time data is less well understood. Timing is fundamental to the effective performance of networked sensors and weapons, where search and fire control radars find, fix and track a target and pass the details of that track to a weapons system to enable it to engage.
Timing also affects frequency.
“Frequency is the first derivative of time,” observes John Fischer, vice president for advanced research and development at Orolia USA. Fischer added that “high precision frequency generation depends on accurate time.”
Track and targeting data is extremely time sensitive. For example, the US Integrated Battle Command System (IBCS) being developed for the US Army by Northrop Grumman consists of a network of radars exchanging target information on missiles travelling at Mach speeds over reliable, low latency networks, integrated with weapons systems that will engage those targets. IBCS can also be connected to up to 23 external networks, such as the US Navy’s Cooperative Engagement Capability (CEC) and Link 16. To be effective, it requires the networks to be synchronized for end-to-end latencies of less than 1 msec. The easiest way to achieve this is through a universally received time signal generated by a GNSS.
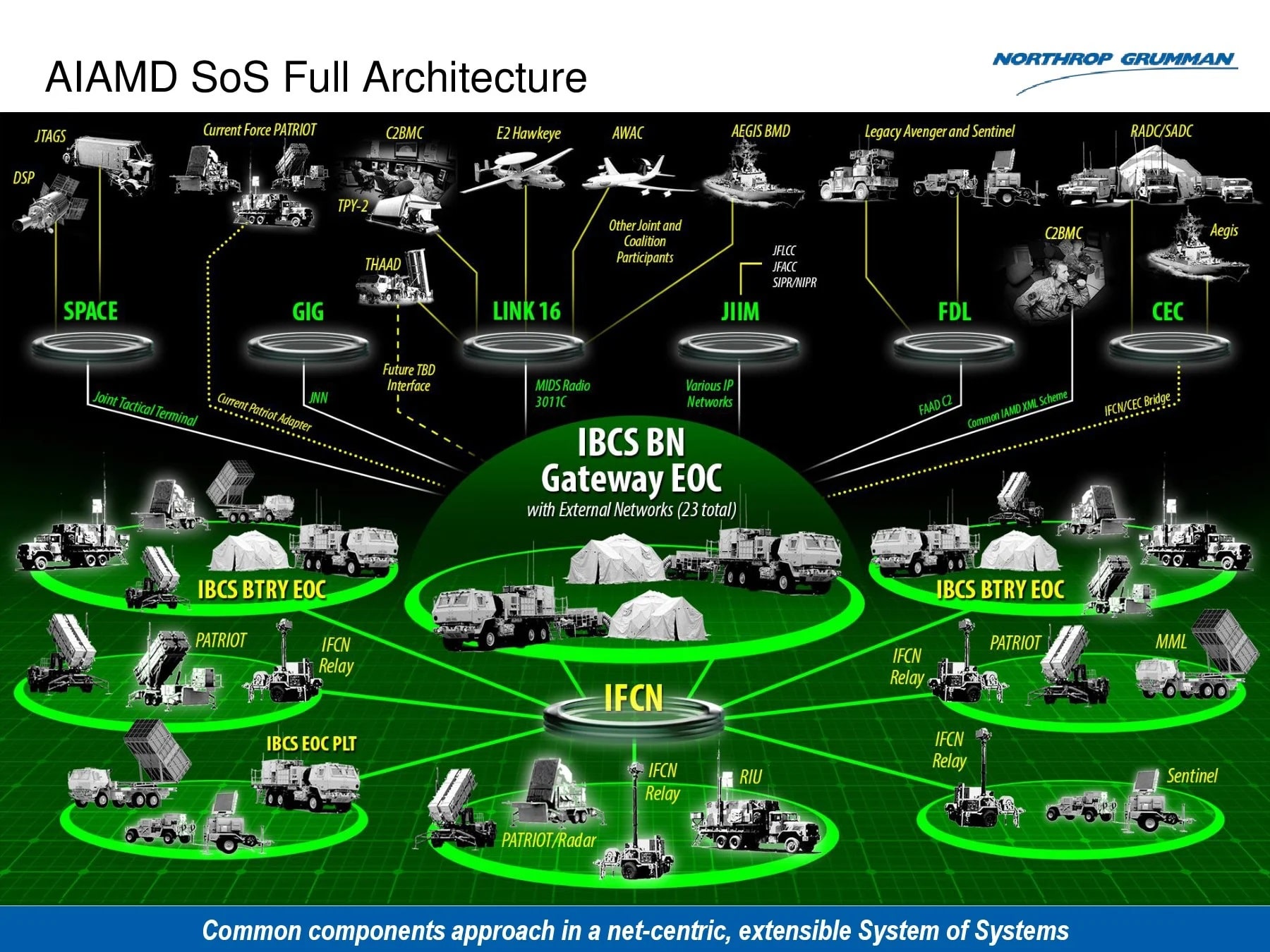
A radar also needs to establish a north azimuth reference, which must be identical across the network to be able to track a target accurately, while integrated weapons systems also need their exact own position and north reference to achieve a successful engagement. GNSS positional data provides this.
The signals transmitted by a GNSS satellite constellation are weak, which can render them vulnerable to jamming or “spoofing” — which is the broadcasting of incorrect but similar signals containing false information that alter either the positional or the timing information — or both. There have been several recent examples of spoofing in the public domain, and these are probably only a proportion of the overall occurrences, because others almost certainly have not been acknowledged.
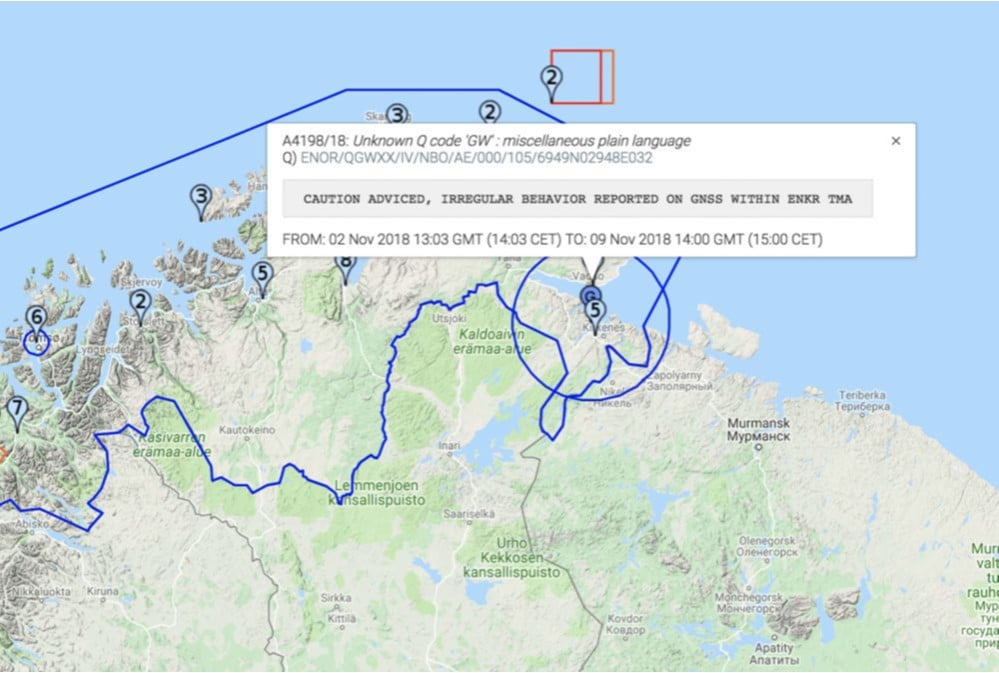
During the Russian exercise “Zapad 2017,” GPS signals were reportedly lost by commercial aircraft and other platforms over the eastern Finnmark region of Norway as far as 250 km from the Russian border, with similar large-scale interferences experienced over land and sea across northern Finland and Sweden. And earlier in the same year it was reported that GPS anomalies affected the navigation of some 20 vessels in the Black Sea, which was suspected to have been caused by a spoofing attack.
In March 2018, a number of maritime incidents were reported in the Eastern Mediterranean, understood to be caused by “GPS interference,” and in November of the same year, Russia was accused by Finland and Norway of jamming GPS signals in their arctic regions during the major NATO exercise, “Trident Juncture.”
Speaking at a symposium in 2019, Colonel Ivan Pavlenko, deputy chief of combat support units of the Joint Staff Armed Forces of Ukraine, said that Ukraine had lost nearly 100 drones to Russian electronic attacks on navigation systems through GPS spoofing. There is also evidence of GPS jamming and spoofing in Syria and elsewhere.
The impact of interference, both jamming and spoofing, on the GPS signal for military operations is fundamental to the mission’s success or failure. The PNT capability delivered by GPS is so essential that it has become a potential single point of failure in all areas of activity. However, the threat can be mitigated and its impact reduced through defensive measures.
The GPS signal can be defended from both jamming and spoofing. The main defense against the former is through advanced antenna technology at the point of reception, while defending the signal against spoofing can be achieved both in transmission and reception.
Detection of interference through jamming is relatively simple. Spoofing is more difficult, but it is possible to detect spoof signals at the receiver because the GPS signal is very hard to reproduce exactly. Anomalies in characteristics can therefore be detected and the false signal identified as such and rejected.
Solutions are available to achieve this. For example, Orolia Defense & Security has developed jamming and spoofing detection software called BroadShield, which is part of Orolia’s extensive Interference, Detection and Mitigation (IDM) suite. The BroadShield algorithms detect interference and anomalies such as jumps in position and time or data inconsistencies within the GPS signal and the GPS spectrum and provide an immediate alert, allowing the host system to take mitigating action.
Orolia Defense & Security has integrated the BroadShield software with a lightweight (46 gram) GPS receiver and antenna called BroadSense to provide a low-SWaP jamming and spoofing detection sensor using the same algorithms. BroadSense shows real-time detection feedback on a screen. It can also provide a custom NMEA output message using a USB connection.
But the strongest defense against spoof signals is encryption at the point of transmission. Encryption should make it impossible to create a false duplicate signal that will deceive the receiver as it effectively creates a closed system between the space segment (the satellite constellation) and the ground segment (the receivers) that is impenetrable to an adversary. Fischer notes that “the big advantage of the encrypted signal is that it is virtually impossible to spoof.”
There are two security architectures for GPS. The P(Y) code signal was mandated from 2006; it can be received by the Selective Availability Anti-Spoofing Module (SAASM) added to a GPS receiver, but still depends on the Coarse/Acquisition (C/A) signal, which is also used extensively by civilian users worldwide. The P(Y) signal is now being superseded by the M-Code signal.
M-Code is designed to give military receivers better defense against jamming, operate in dense vegetation, enhance their ability to track the GPS satellites, support a more secure and flexible cryptography architecture, detect and reject false signals, and provide higher power with comparable availability and accuracy improvements. It also provides military users with a dedicated GPS signal separate from the civilian one, and so once M-Code is fully adopted the world’s dependence on the standard GPS signal will no longer be at risk of interruption by the US military.
There is limited M-Code capability on the Block IIR-M and IIF satellites (19 operational in total) which were launched 2005-2016. Increased capability became available on the Block III GPS satellites the first of which was launched in 2018; four (of ten) are now operational. They provide enhanced signal reliability, accuracy and integrity as well as improved defense against jamming.
The full operational capability of M-Code will be realized with the introduction of the next generation operational control system (OCX) software, which is being installed in the network of 17 global monitoring stations. OCX Block 0, installed at six sites, began trials in June 2020 and operational acceptance for M-Code Early Use (MCEU) was achieved the following November. Further OCX Blocks are in the pipeline – Block 1 software coding was complete in August 2019 – with the transition to full operational capability planned for early 2022.
The new M-Code encryption system is the Modernized Navstar Security Algorithm (MNSA); the latest receivers are known as Military GPS User Equipment (M-GUE). In May 2021 it was announced that the Pentagon had awarded BAE Systems a 10-year $325M contract to provide the US military with MGUE Increment 1 common GPS modules.
To gain maximum benefit from the advantages that M-Code offers, users need to be equipped with M-GUE; indeed, in the US it has been a legal requirement for new military equipment since 2017, although waivers have been available. The Orolia VersaPNT provides a single rugged, Low-SWaP solution that offers M-Code reception together with BroadShield detection capability that can be mounted on a vehicle, providing a hub for the distribution of PNT data on the vehicle’s electronic architecture.

Other equipment is available that can also act as a translator to take M-Code encrypted signals and convert them to the SAASM protocol, or vice versa, creating compatibility between legacy and new equipment. These signals can be rebroadcast using to users in the immediate vicinity. So, a single VersaPNT could provide access to the encrypted M-Code signal for a number of mounted and dismounted users with legacy SAASM receivers.

Orolia Defense & Security also offers the flexible rack-mounted SecureSync M-Code Time Server, which combines time and frequency technology with a dual SAASM and M-Code receiver, specifically aimed at providing an accurate and secure time signal. It includes anti-spoofing and anti-jamming technologies together with an atomic clock and can ingest multiple timing signals in addition to GPS. “SecureSync can output the time signal in every imaginable format,” explained Fischer.

SecureSync with M-Code is already providing time and frequency synchronization for a number of US DoD radar system projects as well as several projects in other NATO countries. For example, In May 2021, Orolia delivered a shipment of M-Code enabled SecureSync mission timing and synchronization units to Lockheed Martin, who was awarded a contract to develop the U.S. Army’s Sentinel A4 system, which is an air and missile defense radar that will provide improved capability against dynamic threats.
As Fischer observes, “M-Code is the next evolutionary step in a very successful GPS program, making both the military and civilian PNT solutions more resilient. In particular, the M-Code encryption provides badly-needed defensive improvements to the GPS signal.”
Supporting Documents




